Before reaping the benefits of IIoT, operators need to gain visibility of the production floor.
Thanks to technological advances that support the potential of Industry 4.0, factory operators are investing more resources into the development of smart factories for enhanced operational efficiency. A recent study showed that the smart factory market is expected to grow 9.33% during the forecast period from 2021 to 2026. But before businesses can reap the benefits of smart factories, operators need to gain visibility of the production floor. This means they need to deploy more sensors and systems at production lines so that engineers can collect sufficient information, develop analytics and take appropriate actions to improve efficiency and connectivity.
Developing a holistic view of production lines requires different types of information. For example, the production status of each production line provides information on how the line is performing and whether potential or existing backlogs exist. By monitoring the real-time production process, users can improve their chances of eliminating potential downtime and enhancing productivity. Tracking the operating condition of machines can help users schedule maintenance tasks without unwanted surprises. Additional sensors can be deployed in production lines to collect temperature and humidity information to help minimize the likelihood of interruptions due to environmental factors (see Figure 1).
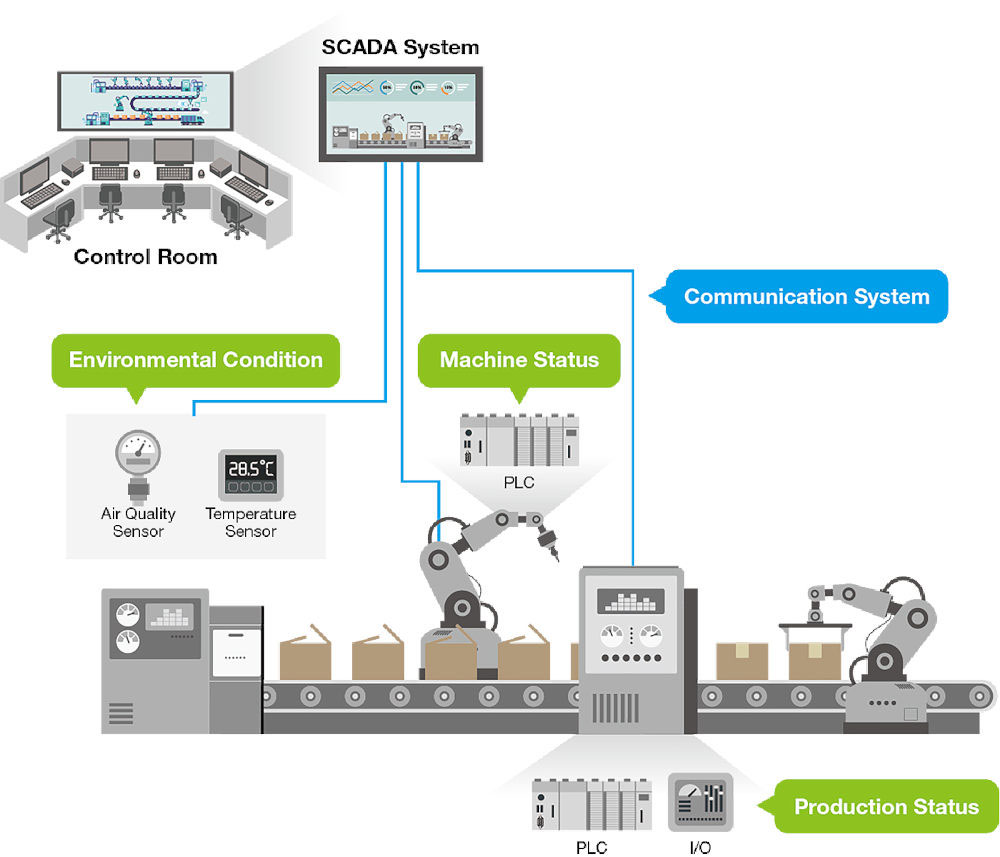
Enabling smooth communication between production lines and the control center can present major challenges for engineers. Without a reliable connection and a solid network implemented between remote sites and the control center, operators cannot receive complete and accurate data for comprehensive planning and optimizing operational efficiency. Consider these suggestions when enabling production line connectivity.
Evaluate connectivity requirements
When enabling connectivity for production lines, figure out what communication interfaces and protocols the field devices use, as well as what systems these devices need to communicate with. The following three scenarios are commonly seen when getting started.
Retrieve operating information from legacy devices. Legacy machines are specifically designed to serve production purposes in factories for decades, but they often come without network interfaces, or they only come with legacy communication interfaces such as serial. Use sensors to capture production information for devices that do not have any communication capability or consider a serial-to-Ethernet solution to retrieve data from legacy devices.
Monitor production status from the control center. Production lines are usually controlled by engineers through a programmable logic controller (PLC) and human-machine interface (HMI) located at the field site. When the central system also needs to control and monitor production lines, they must be able to understand and communicate with the field PLC and HMI. However, machine vendors often adopt communication protocols that might not be compatible with supervisory control and data acquisition (SCADA) systems. Such scenarios require a protocol conversion solution to enable communication between the SCADA system and the PLC and HMI in the field.
Minimize impact from environmental factors. There are various kinds of sensors that can be used to measure environmental conditions such as temperature, humidity and air pressure. These sensors come with multiple input/output (I/O) interfaces and users need a remote I/O solution that can collect information. In addition, pay attention to the supported protocols for remote I/O and choose the one that fits the SCADA system.
No matter what kind of scenario is encountered, there will be a variety of connectivity requirements that need to be fulfilled before data can be received to improve operational efficiency. Carefully evaluate connectivity options and choose the one that not only gets devices and systems connected, but also enables smooth communication with minimal maintenance effort.
Deploy a real-time monitoring network
Enabling a smarter production line requires stronger network capacity and better visibility (see Figure 2). When planning network communication, carefully assess demands on transmission bandwidth, network control capability and manageability for each network node. First, calculate network bandwidth requirements. Connected production lines generally deploy more sensors and systems that generate more data. Huge amounts of data not only require sufficient transmission bandwidth, but also need redundancy to avoid packet loss due to unexpected network downtime.
Second, networking devices require support for communication protocols at the field site and the control center for engineers to monitor and take actions in real time. If adaptive production control systems are being developed or production lines have time-critical processes, consider developing networks based on time-sensitive networking (TSN), the standard Ethernet unified infrastructure, to deliver commands to the right place at the right time.
Finally, deploying numerous network devices leads to tremendous installation and maintenance effort. This is something to consider because it is important to find an efficient solution that simplifies networking management.
Don’t overlook cyberthreats
The growing number of cyberattacks targeting industrial applications in recent years has also made cybersecurity more important than ever. According to one survey, four in 10 manufacturers indicated their operations were affected by a cybersecurity incident in the past 12 months. Threats are everywhere including unauthorized access, unwarranted programs and denial-of-service attacks that could lead to disruption of a production line.
To mitigate security concerns, verify the security level of the networking devices. Use a checklist to verify if a product is secure-by-design. The IEC 62443 standard introduces the concept of security levels that can be applied to zones, conduits, channels and products. The security level (SL) is defined by researching a particular device, and then determining what level of security it should have, depending on its place in the system. Security levels may be classified into four levels 1 to 4, (although the standard also mentions an “open” level 0, which is rarely used):
- Security level 1 (SL1) is a casual exposure.
- Security level 2 (SL2) is an intentional attack with low resources.
- Security level 3 (SL3) is an intentional attack with moderate resources.
- Security level 4 (SL4) is an intentional attack with extensive resources.
In addition, network segmentation is essential to slowing down threat propagation in the event of an actual cyberattack. Network segmentation is a fundamental precaution that can ensure only certain traffic can flow within designated areas. There are several methods to achieve network segmentation. For example, stateful firewalls can help create the first line of defense without needing to change the network topology, which is perceived as friendly for operational technology (OT) environments as they need to operate continuously (see Figure 3). Creating virtual LANs (VLANs) within a larger network also can help segment networks. Another rule of thumb is to implement authentication via 802.1x (AAA/Radius TACACS) and access control via an ACL.
Remote control, monitoring and maintenance have become more prevalent during an OT engineer’s daily operations. Ensuring secure remote access reduces the chance of breaches.
It is crucial to remember that security is a journey, not a one-time event. Constantly monitoring devices and security status and performing vulnerability scans on a regular basis can give users more control over their security posture before mitigation is required.


